Browse our range of reports and publications including performance and financial statement audit reports, assurance review reports, information reports and annual reports.
Internet Security in Australian Government Agencies
The audit objective was to form an opinion on the adequacy of a select group of Australian Government agencies' management of Internet security, including following-up on agencies' implementation of recommendations from the ANAO's 2001 audit. The agencies audited were Australian Customs Service (ACS), Australian Federal Police (AFP), Australian Radiation Protection and Nuclear Safety Agency (ARPANSA), Department of Employment and Workplace Relations (DEWR), Department of Industry, Tourism and Resources (DITR) and Medicare Australia. Factors considered in selecting agencies were agency size based on funding levels, whether the agency was included in ANAO's 2001 audit (ACS, ARPANSA, and DEWR), whether the agency's ICT was managed in-house or outsourced, and the nature of the agency's website (that is, general or restricted access).
Summary
Background
It is Australian Government policy that agencies use the Internet to deliver all appropriate programmes and services1. This policy aims to improve government services for citizens, and to raise the efficiency and reduce the costs of these services.2 This policy has led to government agencies significantly increasing the range, volume and complexity of services delivered via the Internet.
Some agencies provide public information about the agency and its programmes via a website. Other agencies use the Internet to facilitate transactions between the agency and the business sector or between the agency and individuals, which requires higher levels of protection.
While there are many benefits, use of the Internet to provide information and services involves risks for government agencies to manage. These risks have become more acute and electronic attacks more sophisticated over the past few years, and are similar to the risks that private sector companies face in using the Internet in business.
Agencies can maintain Internet security by developing and implementing Information and Communications Technology (ICT) policies, plans and procedures that are derived from risk assessments, and which secure and protect their desktop and server computers.
The Attorney-General's Department Australian Government Protective Security Manual (PSM) 2005 details the minimum standards for the protection of Australian Government information. The PSM states:
All information systems, whether they are paper based or information and communications technology (ICT) systems, used for the processing, storage or transmission of Australian Government official information require some protection to ensure the system's integrity and reliability. This is because, even when the information processed, stored or transmitted by the system is unclassified or authorised for public release, disruption or compromise of the system would prevent or hamper the agency carrying out its functions. The protection for ICT systems should be in accordance with ACSI 33.3
The PSM is supplemented by the Australian Government Information and Communications Technology Security Manual (ACSI 33), which is developed to assist government agencies to achieve an appropriate level of secure information technology. Defence Signals Directorate (DSD) first published the guidelines in 1989. The guidelines include both mandatory requirements and advice. The PSM and ACSI 33 document the Australian Government's protective security policy.
ACSI 33 states that agencies must have consistent security risk assessments, policies and plans for their ICT systems. Figure 1 illustrates ACSI 33 requirements of agencies for their ICT security documentation.
Figure 1 ACSI 33 Information and Communications Technology (ICT) security document requirements
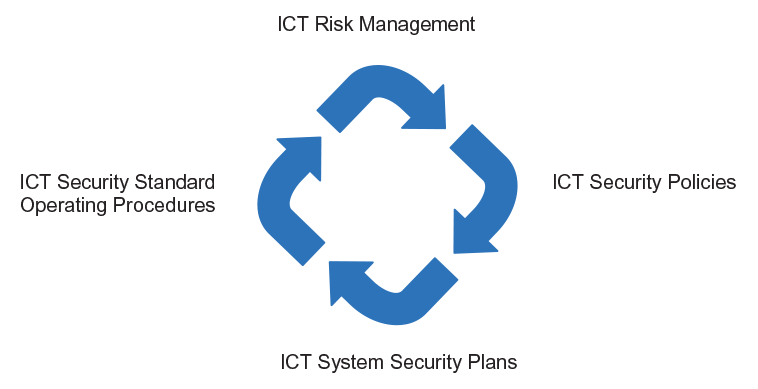
Source: ANAO analysis taking into account the requirements of ACSI 33, showing required documentation and linkages between processes.
Note: ICT Risk Management and ICT Security Policies, presented in sequential steps, are developed in parallel.
2001 performance audit
In 2001, the ANAO completed an audit of Internet Security within Commonwealth Government Agencies.4 The audit concluded that:
security levels across the audited agencies varied significantly from very good to very poor. For the majority of agency websites in the audit, the current level of Internet security is insufficient, given the threat environment and vulnerabilities identified within a number of agency sites. Further, while some agencies had produced good threat and risk assessments and documentation generally, these were not always effectively administered. Overall, a number of agencies could improve performance in some key areas and all agencies could improve performance in one or more aspects of managing Internet security.
Following the 2001 performance audit, the Joint Committee of Public Accounts and Audit held an inquiry into the management and integrity of electronic information within the Australian Government5. The Committee made nine recommendations further emphasising the importance of the security and integrity of electronic information within the Australian Government. The Committee's recommendations were for all Australian Government agencies.
2005 IT Security Management audit
In 2005, the ANAO completed an audit of IT Security Management.6 The audit concluded that:
most agencies had not implemented structured processes to ensure the effective alignment of the IT security policy objectives with organisational risk management processes and Australian Government policy, practices, and standards for the safeguarding of information resources.
That audit examined the framework for management and control of ICT security in eight agencies. The ANAO assessed whether the agencies audited had developed and implemented sound ICT security management principles and practices in accordance with the requirements of the PSM and ACSI 33. The ANAO made five recommendations for agencies to improve ICT security. Those recommendations are relevant to this report.
Audit objective and scope
The audit objective was to form an opinion on the adequacy of a select group of Australian Government agencies' management of Internet security, including following-up on agencies' implementation of recommendations from the ANAO's 2001 audit.
The agencies audited were Australian Customs Service (ACS), Australian Federal Police (AFP), Australian Radiation Protection and Nuclear Safety Agency (ARPANSA), Department of Employment and Workplace Relations (DEWR), Department of Industry, Tourism and Resources (DITR) and Medicare Australia. Factors considered in selecting agencies were agency size based on funding levels, whether the agency was included in ANAO's 2001 audit (ACS, ARPANSA, and DEWR), whether the agency's ICT was managed in-house or outsourced, and the nature of the agency's website (that is, general or restricted access).
The audit was conducted with the assistance of DSD and involved assessing the management of Internet security through reviewing each agency's ICT:
- compliance with Australian Government minimum policy standards and any agency specific policy;
- business continuity and disaster recovery planning;
- contract management where an agency employed a firm or firms to provide ICT services; and
- desktop and server computer standard operating environments, and email filtering.
The audit assessed each agency's ICT security risk assessments and plans, policies and procedures that established the controls for securing an agency's Internet services.
The audit also assessed whether ACS, ARPANSA and DEWR had implemented the recommendations from the 2001 audit relating to risk management, installation of security patches, regular review of system event logs, and keeping ICT documentation current.
The ANAO did not examine agency networks that communicated national security information.
An issues paper was presented to each participating agency. The issues papers assessed each agency's security management framework, risk management, policies, plans and procedures, desktop and server computer standard operating environments, and email filtering. The six issues papers contained 478 suggestions for improvement; 54 relating to ICT risk management, policies and plans, 112 relating to ICT security practices, and 312 relating to desktop and server computer standard operating environments and email filtering.
To safeguard the security of the information held by audited agencies, this report does not name agencies or present details of the ANAO's security findings. Rather, the report examines general issues affecting the security of agencies' use of the Internet, and notes any trends observed across agencies.
Overall audit conclusions
Since the ANAO 2001 performance audit on Internet security, Australian Government agencies have significantly increased the services delivered by the Internet, while ICT risks from within and outside agencies, and the number and sophistication of electronic attacks have grown rapidly. A major risk to Internet security also comes from within agencies, where personnel have the potential to accidentally or deliberately change information.
This environment increases the importance of agencies complying with government policy in the PSM and ACSI 33. Agencies not complying with the PSM and ACSI 33 increase the risks to the confidentiality, integrity and availability of government information, data and systems. Damage may range from embarrassment over website defacement, to unauthorised release of information, and use of a compromised computer to engage in criminal activity.
For the six agencies audited, the ANAO concluded that the current level of Internet security was insufficient, given the risks and problems identified through the audit findings. In particular, none of the audited agencies fully complied with the PSM and ACSI 33. This is similar to the conclusion of the ANAO 2001 audit.
While the size of the ANAO's sample is relatively small, with ten agencies audited in 2001 and six in 2006, the similarity of the conclusions indicates that all Australian Government entities would benefit from a review of their compliance against the PSM and ACSI 33.
A key area in managing Internet security is the administration of new technology, including wireless and voice technologies. Agencies are introducing new technology with the aim of improving productivity and service delivery. Agencies introducing or allowing staff to use new technology within the working environment would benefit from documenting how they balance the risks against the potential benefits. Ordinarily, these would be documented in a business case.
The ANAO noted that a number of agencies could improve performance in some key areas, particularly email filtering, and all agencies audited could improve performance in one or more aspects of managing Internet security, such as the development of system security plans.
The ANAO has made five recommendations based on the audit findings. Given the need for all agencies to effectively manage their use of the Internet, and the similarity of the conclusion in 2001 with the conclusion in this audit, these recommendations are likely to have relevance to the management and operation of ICT security in all Australian Government agencies.
Key Findings
ICT security management
For the six agencies audited, the ANAO found that ICT security documentation did not fully comply with the requirements of the PSM and ACSI 33. Non-compliance identified by the ANAO included:
- no systematic and co-ordinated program for the ongoing management of ICT security-related risk assessments;
- security policies and system security plans were not linked to ICT risk assessments and plans; and
- no system security plans.
Not adhering to the requirements of the PSM and ACSI 33 increases the potential for agency information to be compromised, affecting the agencies' ability to provide services. These findings are consistent with the recommendations from the 2005 ANAO IT Security Management audit report.
The ANAO also found that while several of the six agencies had initiated development of business continuity and disaster recovery plans for their Internet services, only one had sound plans in place. The other agencies had deficiencies that included:
- two agencies largely depended upon the knowledge of key staff and had few documented procedures;
- documents were in draft form; and
- some plans had not been regularly reviewed.
Lack of appropriate business continuity and disaster recovery planning can increase the time taken to recover information after interruptions to an agency's computer system, and lead to agencies being unable to recover critical Internet services quickly, contributing to a failure to deliver services to the community.
The ANAO also concluded that two of the three agencies from the 2001 audit had implemented the recommendations from the audit on risk management and keeping ICT documentation current.
ICT security practices and contract management
The ANAO found that a majority of the six audited agencies had developed and implemented standard operating procedures that covered Internet security. However, standard operating procedures did not always comply with the requirements of ACSI 33.
Key findings of non-compliance identified by the ANAO included:
- inappropriate password management;
- user account privileges inappropriately administered;
- no documented procedures for incident detection and response, management of hardware, and the use of remote access; and
- hardware not adequately secured.
Inadequate management of standard operating procedures increases the risk of the misuse or theft of information, infection of computer systems by malicious code, and use of computer systems to commit fraud.
The ANAO also found that there were particular weaknesses in the management of new technology. For example:
- policy development and supporting procedures for the introduction of new technology, such as USB keys, was generally poor. Where it existed, compliance within agencies was also often poor;
- personnel in one agency were found to be using USB keys to move data from one system to another without documented controls; and
- one agency had developed procedures for procuring USB keys. These procedures were not based on a risk assessment and, accordingly, were incomplete.
When introducing new technology like USB keys, the ANAO also found limited evidence that the agencies were balancing risks against the benefits afforded by new technology. Ordinarily, these would be documented in a business case.
Agencies in managing new technology should conduct risk assessments and develop and implement policies, plans and procedures for their use, and better manage risks to their business.
Four agencies had outsourced their ICT services, and contracts for two of these agencies were poorly drafted and managed. The ANAO identified several weaknesses, including contracts that:
- contained unclear statements on responsibility for development of ICT documentation and procedures;
- contained insufficient detail to adequately monitor performance;
- did not clearly detail what service provider information the agency has the right to review;
- did not provide the agency with full access to the contractor's documentation on the security of the agency's information; and
- allowed inadequate reporting by service providers.
One of the three agencies from the 2001 audit had implemented the recommendation from the audit on regularly reviewing event logs.
ANAO testing of ICT security
For the six agencies audited, the ANAO found that the technical security of each agency's web server 7was adequate. However, all the agencies could improve the security of their desktop computer 8standard operating environments, and improve their email filtering.
Weaknesses identified in the desktop computer standard operating environment included:
- inappropriate access controls, such as users with more access rights than required for their work;
- agency personnel able to download information of their choice from the Internet;
- inadequate auditing of system event logs, including logs that did not record and hold sufficient information for auditing of security events; and
- inappropriate levels of system patching.
As part of the audit methodology, emails were sent to auditee agencies to test whether they bypassed email filters, highlighting any deficiencies in the agencies' email filtering policies or applications. The ANAO found that email filtering in all six agencies was inadequate.
Agencies' responses
The six agencies examined in the audit agreed with the recommendations.
Footnotes
1 National Office for the Information Economy, Better Services, Better Government – The Federal Government's E-government strategy, Canberra, November 2002, p. iii, available at www.agimo.gov.au/_data/assets/pdf_file/35503/ Better_Services-Better_Gov.pdf.
2 Australian Government Information Management Office, Responsive Government: A New Service Agenda, Canberra, March 2005, available at <www. agimo.gov.au/publications/ 2006/march/introduction_to_responsive_government>.
3 Attorney-General's Department, Commonwealth Protective Security Manual 2005, Canberra 2005, Part C, Principle of effective information security practice, 2.6, C3.
4 ANAO Audit Report No.13 2001–2002, (2001), Internet Security within Commonwealth Government Agencies, ANAO, Canberra, available at www.anao.gov.au.
5 Report 399, Enquiry into the Management and Integrity of Electronic Information in the Commonwealth, Joint Committee of Public Accounts and Audit, March 2004, Parliament of Australia, Canberra, available at http://www.aph.gov.au/ house/committee/jpaa/electronic_info/report.htm.
6 ANAO Audit Report No. 23 2005-2006, (2005), IT Security Management, ANAO, Canberra, available at www.anao.gov.au.
7 A web server is a computer that manages and shares web based programmes and services accessible from computers connected to the Internet.
8 A desktop computer is a computer other than a server that is used on a desk in an office or home.